My Attempt At Google CTF for Beginners
The Challenge
Google CTF seemed like a cool challenge so I attempted to solve it this year, having never attempted a CTF before.
The website for the CTF can be found here
My Solutions
Problem 0
- The first problem had an attachment that when unzipped had two files,
log.txtandrand2 log.txtcontained random co-ordinates whilstrand2contained a jumble of text when opened in vim- By doing a search in
rand2forCTFin vim, we find the first flag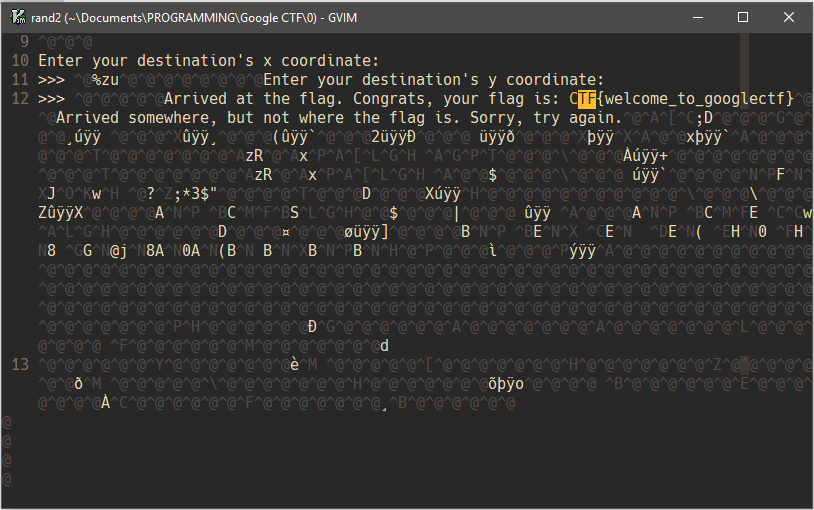
Problem 1
- On the second problem I was redirected to a YouTube video advertising the CTF competition here
- At
0:17, moving frame-by-frame using,and.keys, we can see the next flag
Problem 2
- The next problem was more tricky and required some more domain knowledge
- The zip file contained 2 files this time,
init_satandREADME.pdf README.pdfcontained an image of a satellite with a useful name in it, Osmium
- After looking around the contents of
init_satI realised it was an executable file in Linux, running it on Linux results in a terminal-like UI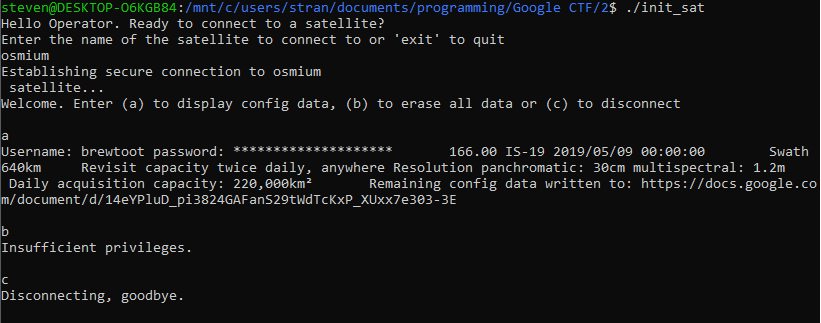
- Opening the Google Docs URL leads to a plain document with just some jumble
of text
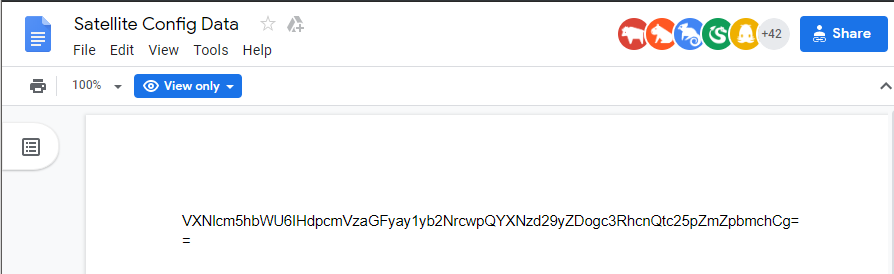
- A common reversible encoding of text is
Base64- so after running the text through a decoder we get some hints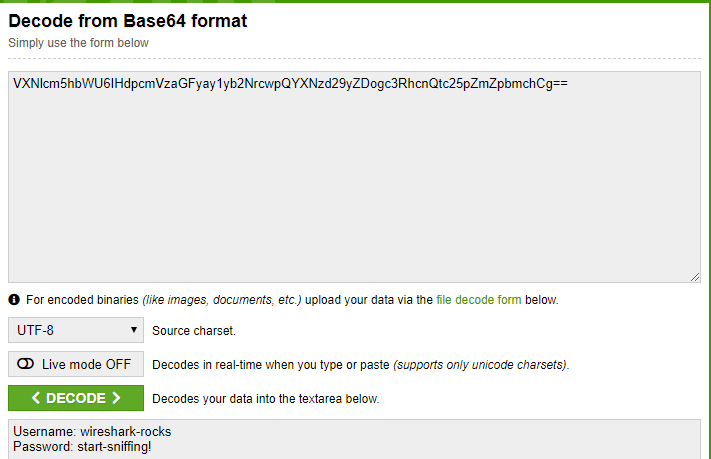
- By re-running
init_satagain with Wireshark open this time we can examine network activity and sniff for any calls made by the program on our network - After looking around we can find some calls that go to
satellite.ctfcompetition.com, by doingFollow > TCP Streamwe can see what the communications are in plain text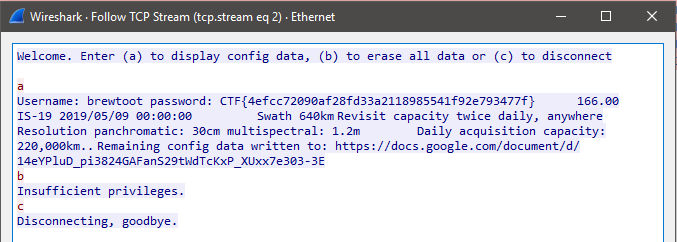
- The flag is finally revealed here
Problem 3
- Coming as soon as I can work it out…